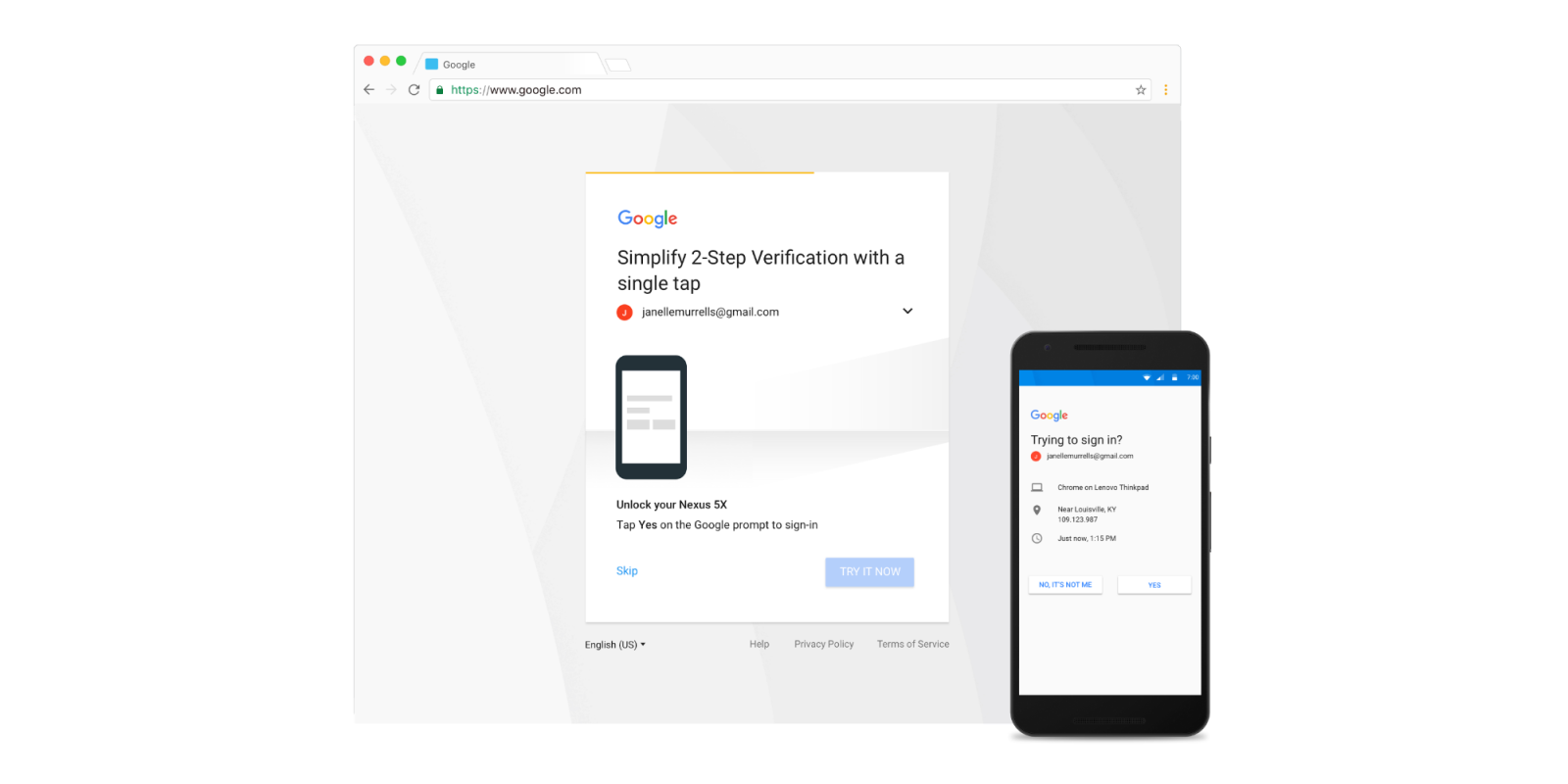
To make users’ accounts more secure, Google has decided to take a significant step by making two-factor authentication compulsory by default. The feature helps users to learn about every login and control the login at the same time.
When a user enables the two-factor authentication option, they will receive a notification on their smartphones regarding the attempt to login into their accounts. Users then easily accept normal logins and reject any fishy login attempts on their accounts.
“One of the best ways to protect your account from a breached or bad password is by having a second form of verification in place – another way for your account to confirm it is really you logging in. Google has been doing this for years, ensuring that your Google Account is protected by multiple layers of verification,” read the blog published by Google.
Users can also use a physical security key like offered by others. Google’s own Titan offers a physical security key feature to secure an account. In 2019, Google made its Andriod smartphones act as an on smart key and later extended to iPhones.
Google’s ambition to offer a future where one doesn’t need a password at all. News of two-factor authentication also announced on World Password Day. According to a survey by Google, 66 percent of Americans still use the same password across multiple sites even after facing multiple hack attempts.
In a country like India, where data laws are not as strong as in the west, news about data leaks hitting media often. Google has tried various initiatives in the country to grow awareness among Indian users. However, many accounts in the country are controlled by a son in a family who often uses similar passwords to control other family accounts.
“One day, we hope stolen passwords will be a thing of the past, because passwords will be a thing of the past, but until then Google will continue to keep you and your passwords safe,” added the blog.